API函数的调用过程(3环部分) 1、Windows API 1.1 Application Programming Interface ,简称 API 函数。 1.2 Windows有多少个API? 主要是存放在 C:\WINDOWS\system32 下面所有的dll
1.3 几个重要的DLL Kernel32.dll: 最核心的功能模块,比如管理内存、进程和线程相关的函数等
User32.dll: 是Windows用户界面相关应用程序接口,如创建窗口和发送消息等
GDI32.dll: 全称是Graphical Device Interface(图形设备接口),包含用于画图和显示文本的函数.比如要显示一个程序窗口,就调用了其中的函数来画这个窗口
Ntdll.dll: 大多数API都会通过这个DLL进入内核(0环)
kernelbase: 函数api作中转的
2、分析ReadProcessMemory 用IDA打开Kernel32.dll,找到ReadProcessMemory函数。win7 为例
整个路线是:
用户程序.exe&ReadProcessMemory
->kernel32&ReadProcessMemory
->kernelbase&ReadProcessMemory
->ntdll&NtReadVirtualMemory
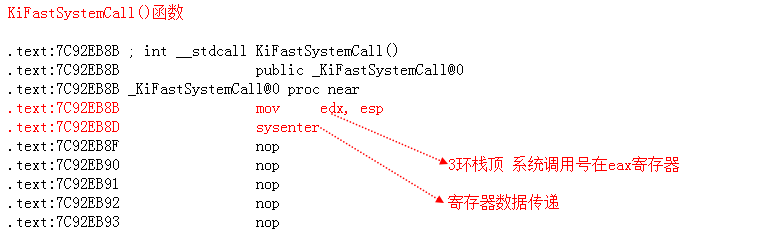
->ntdll&KiFastSystemCall—sysenter
最后这里进入0环老系统老cpu走中断门int 2e,在新系统新cpu里这里进入后则是KiFastCallEntry
[!NOTE]
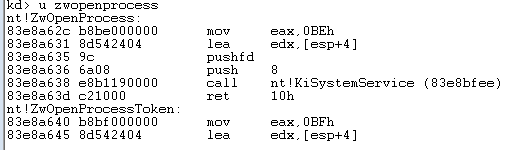
注意:当前的ntdll函数是nt前缀开头,如果是zw开头,则会先走KiSystemService函数,然后在进入KiFastCallEntry2
API函数的调用过程(3环进0环) 1、_KUSER_SHARED_DATA
在 User 层和 Kernel 层分别定义了一个 KUSER_SHARED_DATA 结构区域,用于 User 层和 Kernel 层共享某些数据
它们使用固定的地址值映射,_KUSER_SHARED_DATA 结构区域在 User 和 Kernel 层地址分别为
1 2 User 层地址为:0x7ffe0000 Kernnel 层地址为:0xffdf0000
[!NOTE]
特别说明:
2、0x7FFE0300 当通过eax=1来执行cpuid指令时,处理器的特征信息被放在ecx和edx寄存器中,其中edx包含了一个SEP位(11位),该位指明了当前处理器知否支持
sysenter/sysexit 指令
支持:ntdll.dll!KiFastSystemCall()
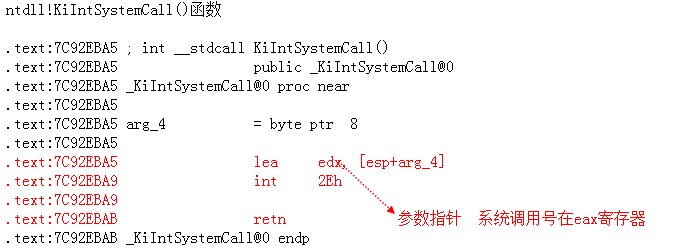
不支持:ntdll.dll!KiIntSystemCall()
3、进0环需要更改哪些寄存器?
CS的权限由3变为0 意味着需要新的CS
SS与CS的权限永远一致 需要新的SS
权限发生切换的时候,堆栈也一定会切换,需要新的ESP
进0环后代码的位置,需要EIP
4、中断门进0环
4.1 INT 0x2E进0环 步骤一:在IDT表中找到0x2E号门描述符
步骤二:分析CS/SS/ESP/EIP的来源
步骤三:分析EIP是什么
5、快速调用进0环
中断门进0环,需要的CS、EIP在IDT表中,需要查内存(SS与ESP由TSS提供)
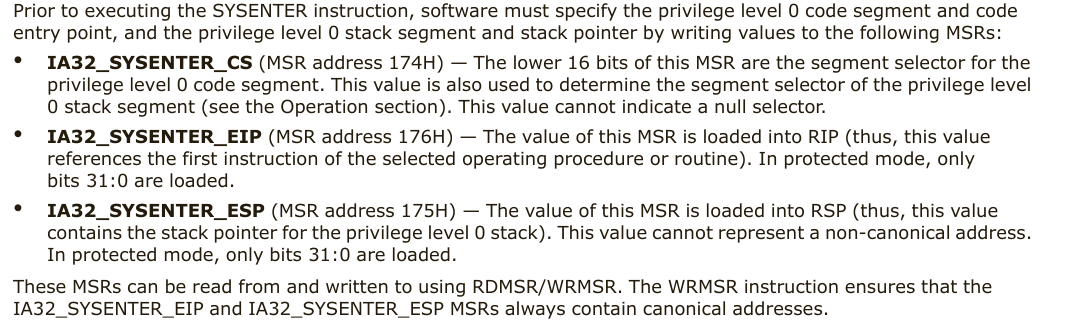
CPU如果支持sysenter 指令时,操作系统会提前将CS/SS/ESP/EIP的值存储在MSR寄存器 中,sysenter指令执行时,CPU会将MSR寄存器中的值直接写入相关寄存器 ,没有读内存 的过程,所以叫快速调用
5.1 sysenter进0环 在执行sysenter指令之前,操作系统必须指定0环的CS段、SS段、EIP以及ESP
MSR 地址
IA32_SYSENTER_CS
174H
IA32_SYSENTER_ESP
175H
IA32_SYSENTER_EIP
176H
1 2 3 4 5 RDMSR/WRMST来进行读写(操作系统使用WRMST写该寄存器): kd> rdmsr 174 //查看CS kd> rdmsr 175 //查看ESP kd> rdmsr 176 //查看EIP
具体参考intel白皮书:第二卷
6、总结 6.1 API通过中断门进0环
固定中断号为0x2E
CS/EIP由门描述符提供 ESP/SS由TSS提供
进入0环后执行的内核函数:NT!KiSystemService
6.2 API通过sysenter指令进0环
CS/ESP/EIP由MSR寄存器提供(SS是算出来的 )
进入0环后执行的内核函数:NT!KiFastCallEntry
内核模块:ntoskrnl.exe/ntkrnlpa.exe
进0环前保存现场 _Trap_Frame结构
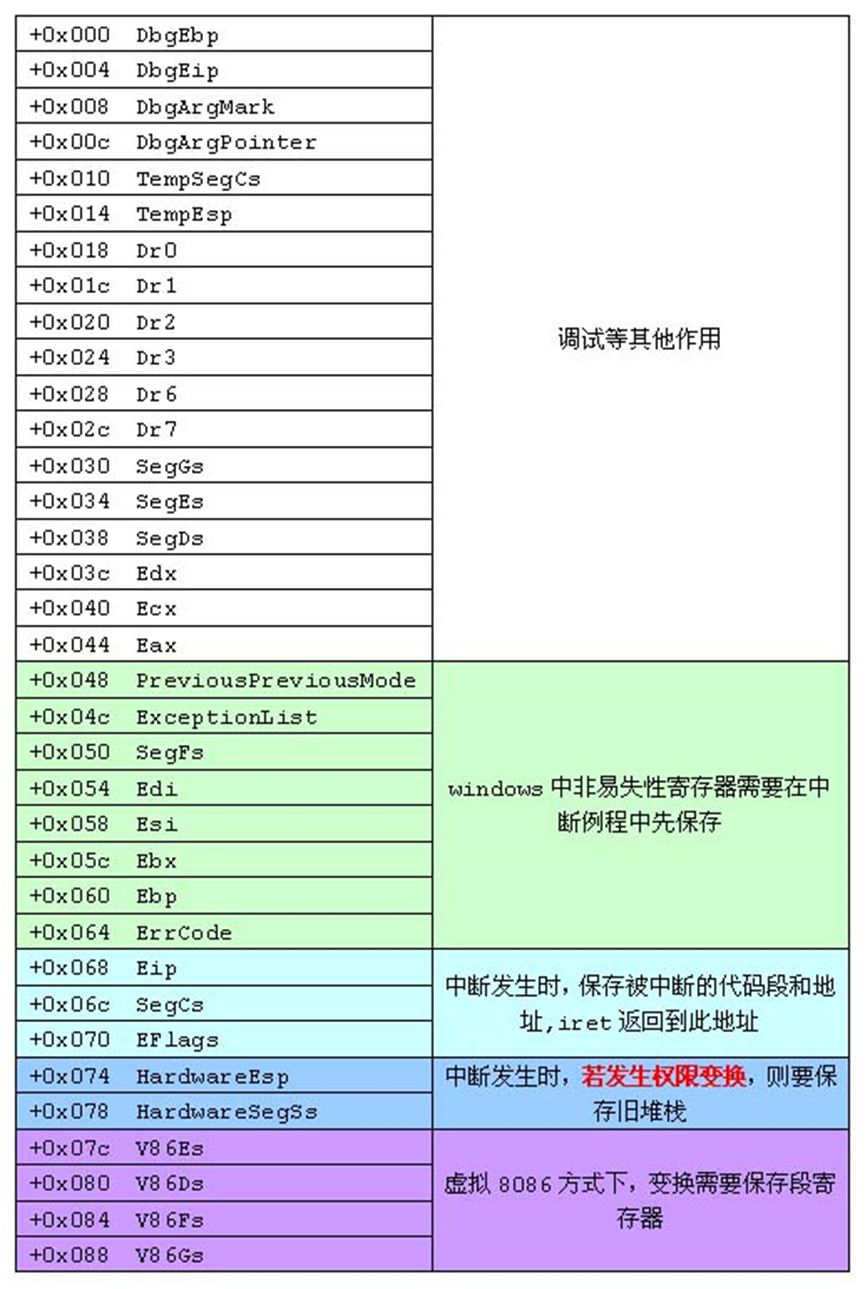
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 typedef struct _KTRAP_FRAME {0x000 ULONG DbgEbp; 0x004 ULONG DbgEip; 0x008 ULONG DbgArgMark; 0x00c ULONG DbgArgPointer; 0x010 ULONG TempSegCs;0x014 ULONG TempEsp;0x018 ULONG Dr0;0x01c ULONG Dr1;0x020 ULONG Dr2;0x024 ULONG Dr3;0x028 ULONG Dr6;0x02c ULONG Dr7;0x030 ULONG SegGs;0x034 ULONG SegEs;0x038 ULONG SegDs;0x03c ULONG Edx;0x040 ULONG Ecx;0x044 ULONG Eax;0x048 ULONG PreviousPreviousMode;0x04c PEXCEPTION_REGISTRATION_RECORD ExceptionList; 0x050 ULONG SegFs;0x054 ULONG Edi;0x058 ULONG Esi;0x05c ULONG Ebx;0x060 ULONG Ebp;0x064 ULONG ErrCode;0x068 ULONG Eip;0x06c ULONG SegCs;0x070 ULONG EFlags;0x074 ULONG HardwareEsp; 0x078 ULONG HardwareSegSs; 0x07c ULONG V86Es; 0x080 ULONG V86Ds; 0x084 ULONG V86Fs;0x08c ULONG V86Gs;} KTRAP_FRAME;
其中0x064 ULONG ErrCode;参考白皮书第三卷
_ETHREAD结构 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 nt!_ETHREAD +0x000 Tcb : _KTHREAD +0x200 CreateTime : _LARGE_INTEGER +0x208 ExitTime : _LARGE_INTEGER +0x208 KeyedWaitChain : _LIST_ENTRY +0x210 ExitStatus : Int4B +0x214 PostBlockList : _LIST_ENTRY +0x214 ForwardLinkShadow : Ptr32 Void +0x218 StartAddress : Ptr32 Void +0x21c TerminationPort : Ptr32 _TERMINATION_PORT +0x21c ReaperLink : Ptr32 _ETHREAD +0x21c KeyedWaitValue : Ptr32 Void +0x220 ActiveTimerListLock : Uint4B +0x224 ActiveTimerListHead : _LIST_ENTRY +0x22c Cid : _CLIENT_ID +0x234 KeyedWaitSemaphore : _KSEMAPHORE +0x234 AlpcWaitSemaphore : _KSEMAPHORE +0x248 ClientSecurity : _PS_CLIENT_SECURITY_CONTEXT +0x24c IrpList : _LIST_ENTRY +0x254 TopLevelIrp : Uint4B +0x258 DeviceToVerify : Ptr32 _DEVICE_OBJECT +0x25c CpuQuotaApc : Ptr32 _PSP_CPU_QUOTA_APC +0x260 Win32StartAddress : Ptr32 Void +0x264 LegacyPowerObject : Ptr32 Void +0x268 ThreadListEntry : _LIST_ENTRY +0x270 RundownProtect : _EX_RUNDOWN_REF +0x274 ThreadLock : _EX_PUSH_LOCK +0x278 ReadClusterSize : Uint4B +0x27c MmLockOrdering : Int4B +0x280 CrossThreadFlags : Uint4B +0x280 Terminated : Pos 0 , 1 Bit +0x280 ThreadInserted : Pos 1 , 1 Bit +0x280 HideFromDebugger : Pos 2 , 1 Bit +0x280 ActiveImpersonationInfo : Pos 3 , 1 Bit +0x280 Reserved : Pos 4 , 1 Bit +0x280 HardErrorsAreDisabled : Pos 5 , 1 Bit +0x280 BreakOnTermination : Pos 6 , 1 Bit +0x280 SkipCreationMsg : Pos 7 , 1 Bit +0x280 SkipTerminationMsg : Pos 8 , 1 Bit +0x280 CopyTokenOnOpen : Pos 9 , 1 Bit +0x280 ThreadIoPriority : Pos 10 , 3 Bits +0x280 ThreadPagePriority : Pos 13 , 3 Bits +0x280 RundownFail : Pos 16 , 1 Bit +0x280 NeedsWorkingSetAging : Pos 17 , 1 Bit +0x284 SameThreadPassiveFlags : Uint4B +0x284 ActiveExWorker : Pos 0 , 1 Bit +0x284 ExWorkerCanWaitUser : Pos 1 , 1 Bit +0x284 MemoryMaker : Pos 2 , 1 Bit +0x284 ClonedThread : Pos 3 , 1 Bit +0x284 KeyedEventInUse : Pos 4 , 1 Bit +0x284 RateApcState : Pos 5 , 2 Bits +0x284 SelfTerminate : Pos 7 , 1 Bit +0x288 SameThreadApcFlags : Uint4B +0x288 Spare : Pos 0 , 1 Bit +0x288 StartAddressInvalid : Pos 1 , 1 Bit +0x288 EtwPageFaultCalloutActive : Pos 2 , 1 Bit +0x288 OwnsProcessWorkingSetExclusive : Pos 3 , 1 Bit +0x288 OwnsProcessWorkingSetShared : Pos 4 , 1 Bit +0x288 OwnsSystemCacheWorkingSetExclusive : Pos 5 , 1 Bit +0x288 OwnsSystemCacheWorkingSetShared : Pos 6 , 1 Bit +0x288 OwnsSessionWorkingSetExclusive : Pos 7 , 1 Bit +0x289 OwnsSessionWorkingSetShared : Pos 0 , 1 Bit +0x289 OwnsProcessAddressSpaceExclusive : Pos 1 , 1 Bit +0x289 OwnsProcessAddressSpaceShared : Pos 2 , 1 Bit +0x289 SuppressSymbolLoad : Pos 3 , 1 Bit +0x289 Prefetching : Pos 4 , 1 Bit +0x289 OwnsDynamicMemoryShared : Pos 5 , 1 Bit +0x289 OwnsChangeControlAreaExclusive : Pos 6 , 1 Bit +0x289 OwnsChangeControlAreaShared : Pos 7 , 1 Bit +0x28a OwnsPagedPoolWorkingSetExclusive : Pos 0 , 1 Bit +0x28a OwnsPagedPoolWorkingSetShared : Pos 1 , 1 Bit +0x28a OwnsSystemPtesWorkingSetExclusive : Pos 2 , 1 Bit +0x28a OwnsSystemPtesWorkingSetShared : Pos 3 , 1 Bit +0x28a TrimTrigger : Pos 4 , 2 Bits +0x28a Spare1 : Pos 6 , 2 Bits +0x28b PriorityRegionActive : UChar +0x28c CacheManagerActive : UChar +0x28d DisablePageFaultClustering : UChar +0x28e ActiveFaultCount : UChar +0x28f LockOrderState : UChar +0x290 AlpcMessageId : Uint4B +0x294 AlpcMessage : Ptr32 Void +0x294 AlpcReceiveAttributeSet : Uint4B +0x298 AlpcWaitListEntry : _LIST_ENTRY +0x2a0 CacheManagerCount : Uint4B +0x2a4 IoBoostCount : Uint4B +0x2a8 IrpListLock : Uint4B +0x2ac ReservedForSynchTracking : Ptr32 Void +0x2b0 CmCallbackListHead : _SINGLE_LIST_ENTRY
_KTHREAD结构 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 kd> dt _KTHREAD nt!_KTHREAD +0x000 Header : _DISPATCHER_HEADER +0x010 CycleTime : Uint8B +0x018 HighCycleTime : Uint4B +0x020 QuantumTarget : Uint8B +0x028 InitialStack : Ptr32 Void +0x02c StackLimit : Ptr32 Void +0x030 KernelStack : Ptr32 Void +0x034 ThreadLock : Uint4B +0x038 WaitRegister : _KWAIT_STATUS_REGISTER +0x039 Running : UChar +0x03a Alerted : [2 ] UChar +0x03c KernelStackResident : Pos 0 , 1 Bit +0x03c ReadyTransition : Pos 1 , 1 Bit +0x03c ProcessReadyQueue : Pos 2 , 1 Bit +0x03c WaitNext : Pos 3 , 1 Bit +0x03c SystemAffinityActive : Pos 4 , 1 Bit +0x03c Alertable : Pos 5 , 1 Bit +0x03c GdiFlushActive : Pos 6 , 1 Bit +0x03c UserStackWalkActive : Pos 7 , 1 Bit +0x03c ApcInterruptRequest : Pos 8 , 1 Bit +0x03c ForceDeferSchedule : Pos 9 , 1 Bit +0x03c QuantumEndMigrate : Pos 10 , 1 Bit +0x03c UmsDirectedSwitchEnable : Pos 11 , 1 Bit +0x03c TimerActive : Pos 12 , 1 Bit +0x03c SystemThread : Pos 13 , 1 Bit +0x03c Reserved : Pos 14 , 18 Bits +0x03c MiscFlags : Int4B +0x040 ApcState : _KAPC_STATE +0x040 ApcStateFill : [23 ] UChar +0x057 Priority : Char +0x058 NextProcessor : Uint4B +0x05c DeferredProcessor : Uint4B +0x060 ApcQueueLock : Uint4B +0x064 ContextSwitches : Uint4B +0x068 State : UChar +0x069 NpxState : Char +0x06a WaitIrql : UChar +0x06b WaitMode : Char +0x06c WaitStatus : Int4B +0x070 WaitBlockList : Ptr32 _KWAIT_BLOCK +0x074 WaitListEntry : _LIST_ENTRY +0x074 SwapListEntry : _SINGLE_LIST_ENTRY +0x07c Queue : Ptr32 _KQUEUE +0x080 WaitTime : Uint4B +0x084 KernelApcDisable : Int2B +0x086 SpecialApcDisable : Int2B +0x084 CombinedApcDisable : Uint4B +0x088 Teb : Ptr32 Void +0x090 Timer : _KTIMER +0x0b8 AutoAlignment : Pos 0 , 1 Bit +0x0b8 DisableBoost : Pos 1 , 1 Bit +0x0b8 EtwStackTraceApc1Inserted : Pos 2 , 1 Bit +0x0b8 EtwStackTraceApc2Inserted : Pos 3 , 1 Bit +0x0b8 CalloutActive : Pos 4 , 1 Bit +0x0b8 ApcQueueable : Pos 5 , 1 Bit +0x0b8 EnableStackSwap : Pos 6 , 1 Bit +0x0b8 GuiThread : Pos 7 , 1 Bit +0x0b8 UmsPerformingSyscall : Pos 8 , 1 Bit +0x0b8 VdmSafe : Pos 9 , 1 Bit +0x0b8 UmsDispatched : Pos 10 , 1 Bit +0x0b8 ReservedFlags : Pos 11 , 21 Bits +0x0b8 ThreadFlags : Int4B +0x0bc ServiceTable : Ptr32 Void +0x0c0 WaitBlock : [4 ] _KWAIT_BLOCK +0x120 QueueListEntry : _LIST_ENTRY +0x128 TrapFrame : Ptr32 _KTRAP_FRAME +0x12c FirstArgument : Ptr32 Void +0x130 CallbackStack : Ptr32 Void +0x130 CallbackDepth : Uint4B +0x134 ApcStateIndex : UChar +0x135 BasePriority : Char +0x136 PriorityDecrement : Char +0x136 ForegroundBoost : Pos 0 , 4 Bits +0x136 UnusualBoost : Pos 4 , 4 Bits +0x137 Preempted : UChar +0x138 AdjustReason : UChar +0x139 AdjustIncrement : Char +0x13a PreviousMode : Char +0x13b Saturation : Char +0x13c SystemCallNumber : Uint4B +0x140 FreezeCount : Uint4B +0x144 UserAffinity : _GROUP_AFFINITY +0x150 Process : Ptr32 _KPROCESS +0x154 Affinity : _GROUP_AFFINITY +0x160 IdealProcessor : Uint4B +0x164 UserIdealProcessor : Uint4B +0x168 ApcStatePointer : [2 ] Ptr32 _KAPC_STATE +0x170 SavedApcState : _KAPC_STATE +0x170 SavedApcStateFill : [23 ] UChar +0x187 WaitReason : UChar +0x188 SuspendCount : Char +0x189 Spare1 : Char +0x18a OtherPlatformFill : UChar +0x18c Win32Thread : Ptr32 Void +0x190 StackBase : Ptr32 Void +0x194 SuspendApc : _KAPC +0x194 SuspendApcFill0 : [1 ] UChar +0x195 ResourceIndex : UChar +0x194 SuspendApcFill1 : [3 ] UChar +0x197 QuantumReset : UChar +0x194 SuspendApcFill2 : [4 ] UChar +0x198 KernelTime : Uint4B +0x194 SuspendApcFill3 : [36 ] UChar +0x1b8 WaitPrcb : Ptr32 _KPRCB +0x194 SuspendApcFill4 : [40 ] UChar +0x1bc LegoData : Ptr32 Void +0x194 SuspendApcFill5 : [47 ] UChar +0x1c3 LargeStack : UChar +0x1c4 UserTime : Uint4B +0x1c8 SuspendSemaphore : _KSEMAPHORE +0x1c8 SuspendSemaphorefill : [20 ] UChar +0x1dc SListFaultCount : Uint4B +0x1e0 ThreadListEntry : _LIST_ENTRY +0x1e8 MutantListHead : _LIST_ENTRY +0x1f0 SListFaultAddress : Ptr32 Void +0x1f4 ThreadCounters : Ptr32 _KTHREAD_COUNTERS +0x1f8 XStateSave : Ptr32 _XSTATE_SAVE
_KPCR结构 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 nt!_KPCR +0x000 NtTib : _NT_TIB +0x000 Used_ExceptionList : Ptr32 _EXCEPTION_REGISTRATION_RECORD +0x004 Used_StackBase : Ptr32 Void +0x008 Spare2 : Ptr32 Void +0x00c TssCopy : Ptr32 Void +0x010 ContextSwitches : Uint4B +0x014 SetMemberCopy : Uint4B +0x018 Used_Self : Ptr32 Void +0x01c SelfPcr : Ptr32 _KPCR +0x020 Prcb : Ptr32 _KPRCB +0x024 Irql : UChar +0x028 IRR : Uint4B +0x02c IrrActive : Uint4B +0x030 IDR : Uint4B +0x034 KdVersionBlock : Ptr32 Void +0x038 IDT : Ptr32 _KIDTENTRY +0x03c GDT : Ptr32 _KGDTENTRY +0x040 TSS : Ptr32 _KTSS +0x044 MajorVersion : Uint2B +0x046 MinorVersion : Uint2B +0x048 SetMember : Uint4B +0x04c StallScaleFactor : Uint4B +0x050 SpareUnused : UChar +0x051 Number : UChar +0x052 Spare0 : UChar +0x053 SecondLevelCacheAssociativity : UChar +0x054 VdmAlert : Uint4B +0x058 KernelReserved : [14 ] Uint4B +0x090 SecondLevelCacheSize : Uint4B +0x094 HalReserved : [16 ] Uint4B +0x0d4 InterruptMode : Uint4B +0x0d8 Spare1 : UChar +0x0dc KernelReserved2 : [17 ] Uint4B +0x120 PrcbData : _KPRCB
_NT_TIB结构 1 2 3 4 5 6 7 8 9 nt!_NT_TIB +0x000 ExceptionList : Ptr32 _EXCEPTION_REGISTRATION_RECORD +0x004 StackBase : Ptr32 Void +0x008 StackLimit : Ptr32 Void +0x00c SubSystemTib : Ptr32 Void +0x010 FiberData : Ptr32 Void +0x010 Version : Uint4B +0x014 ArbitraryUserPointer : Ptr32 Void +0x018 Self : Ptr32 _NT_TIB
_KPRCB结构 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 nt!_KPRCB +0x000 MinorVersion : Uint2B +0x002 MajorVersion : Uint2B +0x004 CurrentThread : Ptr32 _KTHREAD +0x008 NextThread : Ptr32 _KTHREAD +0x00c IdleThread : Ptr32 _KTHREAD +0x010 LegacyNumber : UChar +0x011 NestingLevel : UChar +0x012 BuildType : Uint2B +0x014 CpuType : Char +0x015 CpuID : Char +0x016 CpuStep : Uint2B +0x016 CpuStepping : UChar +0x017 CpuModel : UChar +0x018 ProcessorState : _KPROCESSOR_STATE +0x338 KernelReserved : [16 ] Uint4B +0x378 HalReserved : [16 ] Uint4B +0x3b8 CFlushSize : Uint4B +0x3bc CoresPerPhysicalProcessor : UChar +0x3bd LogicalProcessorsPerCore : UChar +0x3be PrcbPad0 : [2 ] UChar +0x3c0 MHz : Uint4B +0x3c4 CpuVendor : UChar +0x3c5 GroupIndex : UChar +0x3c6 Group : Uint2B +0x3c8 GroupSetMember : Uint4B +0x3cc Number : Uint4B +0x3d0 PrcbPad1 : [72 ] UChar +0x418 LockQueue : [17 ] _KSPIN_LOCK_QUEUE +0x4a0 NpxThread : Ptr32 _KTHREAD +0x4a4 InterruptCount : Uint4B +0x4a8 KernelTime : Uint4B +0x4ac UserTime : Uint4B +0x4b0 DpcTime : Uint4B +0x4b4 DpcTimeCount : Uint4B +0x4b8 InterruptTime : Uint4B +0x4bc AdjustDpcThreshold : Uint4B +0x4c0 PageColor : Uint4B +0x4c4 DebuggerSavedIRQL : UChar +0x4c5 NodeColor : UChar +0x4c6 PrcbPad20 : [2 ] UChar +0x4c8 NodeShiftedColor : Uint4B +0x4cc ParentNode : Ptr32 _KNODE +0x4d0 SecondaryColorMask : Uint4B +0x4d4 DpcTimeLimit : Uint4B +0x4d8 PrcbPad21 : [2 ] Uint4B +0x4e0 CcFastReadNoWait : Uint4B +0x4e4 CcFastReadWait : Uint4B +0x4e8 CcFastReadNotPossible : Uint4B +0x4ec CcCopyReadNoWait : Uint4B +0x4f0 CcCopyReadWait : Uint4B +0x4f4 CcCopyReadNoWaitMiss : Uint4B +0x4f8 MmSpinLockOrdering : Int4B +0x4fc IoReadOperationCount : Int4B +0x500 IoWriteOperationCount : Int4B +0x504 IoOtherOperationCount : Int4B +0x508 IoReadTransferCount : _LARGE_INTEGER +0x510 IoWriteTransferCount : _LARGE_INTEGER +0x518 IoOtherTransferCount : _LARGE_INTEGER +0x520 CcFastMdlReadNoWait : Uint4B +0x524 CcFastMdlReadWait : Uint4B +0x528 CcFastMdlReadNotPossible : Uint4B +0x52c CcMapDataNoWait : Uint4B +0x530 CcMapDataWait : Uint4B +0x534 CcPinMappedDataCount : Uint4B +0x538 CcPinReadNoWait : Uint4B +0x53c CcPinReadWait : Uint4B +0x540 CcMdlReadNoWait : Uint4B +0x544 CcMdlReadWait : Uint4B +0x548 CcLazyWriteHotSpots : Uint4B +0x54c CcLazyWriteIos : Uint4B +0x550 CcLazyWritePages : Uint4B +0x554 CcDataFlushes : Uint4B +0x558 CcDataPages : Uint4B +0x55c CcLostDelayedWrites : Uint4B +0x560 CcFastReadResourceMiss : Uint4B +0x564 CcCopyReadWaitMiss : Uint4B +0x568 CcFastMdlReadResourceMiss : Uint4B +0x56c CcMapDataNoWaitMiss : Uint4B +0x570 CcMapDataWaitMiss : Uint4B +0x574 CcPinReadNoWaitMiss : Uint4B +0x578 CcPinReadWaitMiss : Uint4B +0x57c CcMdlReadNoWaitMiss : Uint4B +0x580 CcMdlReadWaitMiss : Uint4B +0x584 CcReadAheadIos : Uint4B +0x588 KeAlignmentFixupCount : Uint4B +0x58c KeExceptionDispatchCount : Uint4B +0x590 KeSystemCalls : Uint4B +0x594 AvailableTime : Uint4B +0x598 PrcbPad22 : [2 ] Uint4B +0x5a0 PPLookasideList : [16 ] _PP_LOOKASIDE_LIST +0x620 PPNPagedLookasideList : [32 ] _GENERAL_LOOKASIDE_POOL +0xf20 PPPagedLookasideList : [32 ] _GENERAL_LOOKASIDE_POOL +0x1820 PacketBarrier : Uint4B +0x1824 ReverseStall : Int4B +0x1828 IpiFrame : Ptr32 Void +0x182c PrcbPad3 : [52 ] UChar +0x1860 CurrentPacket : [3 ] Ptr32 Void +0x186c TargetSet : Uint4B +0x1870 WorkerRoutine : Ptr32 void +0x1874 IpiFrozen : Uint4B +0x1878 PrcbPad4 : [40 ] UChar +0x18a0 RequestSummary : Uint4B +0x18a4 SignalDone : Ptr32 _KPRCB +0x18a8 PrcbPad50 : [56 ] UChar +0x18e0 DpcData : [2 ] _KDPC_DATA +0x1908 DpcStack : Ptr32 Void +0x190c MaximumDpcQueueDepth : Int4B +0x1910 DpcRequestRate : Uint4B +0x1914 MinimumDpcRate : Uint4B +0x1918 DpcLastCount : Uint4B +0x191c PrcbLock : Uint4B +0x1920 DpcGate : _KGATE +0x1930 ThreadDpcEnable : UChar +0x1931 QuantumEnd : UChar +0x1932 DpcRoutineActive : UChar +0x1933 IdleSchedule : UChar +0x1934 DpcRequestSummary : Int4B +0x1934 DpcRequestSlot : [2 ] Int2B +0x1934 NormalDpcState : Int2B +0x1936 DpcThreadActive : Pos 0 , 1 Bit +0x1936 ThreadDpcState : Int2B +0x1938 TimerHand : Uint4B +0x193c LastTick : Uint4B +0x1940 MasterOffset : Int4B +0x1944 PrcbPad41 : [2 ] Uint4B +0x194c PeriodicCount : Uint4B +0x1950 PeriodicBias : Uint4B +0x1958 TickOffset : Uint8B +0x1960 TimerTable : _KTIMER_TABLE +0x31a0 CallDpc : _KDPC +0x31c0 ClockKeepAlive : Int4B +0x31c4 ClockCheckSlot : UChar +0x31c5 ClockPollCycle : UChar +0x31c6 PrcbPad6 : [2 ] UChar +0x31c8 DpcWatchdogPeriod : Int4B +0x31cc DpcWatchdogCount : Int4B +0x31d0 ThreadWatchdogPeriod : Int4B +0x31d4 ThreadWatchdogCount : Int4B +0x31d8 KeSpinLockOrdering : Int4B +0x31dc PrcbPad70 : [1 ] Uint4B +0x31e0 WaitListHead : _LIST_ENTRY +0x31e8 WaitLock : Uint4B +0x31ec ReadySummary : Uint4B +0x31f0 QueueIndex : Uint4B +0x31f4 DeferredReadyListHead : _SINGLE_LIST_ENTRY +0x31f8 StartCycles : Uint8B +0x3200 CycleTime : Uint8B +0x3208 HighCycleTime : Uint4B +0x320c PrcbPad71 : Uint4B +0x3210 PrcbPad72 : [2 ] Uint8B +0x3220 DispatcherReadyListHead : [32 ] _LIST_ENTRY +0x3320 ChainedInterruptList : Ptr32 Void +0x3324 LookasideIrpFloat : Int4B +0x3328 MmPageFaultCount : Int4B +0x332c MmCopyOnWriteCount : Int4B +0x3330 MmTransitionCount : Int4B +0x3334 MmCacheTransitionCount : Int4B +0x3338 MmDemandZeroCount : Int4B +0x333c MmPageReadCount : Int4B +0x3340 MmPageReadIoCount : Int4B +0x3344 MmCacheReadCount : Int4B +0x3348 MmCacheIoCount : Int4B +0x334c MmDirtyPagesWriteCount : Int4B +0x3350 MmDirtyWriteIoCount : Int4B +0x3354 MmMappedPagesWriteCount : Int4B +0x3358 MmMappedWriteIoCount : Int4B +0x335c CachedCommit : Uint4B +0x3360 CachedResidentAvailable : Uint4B +0x3364 HyperPte : Ptr32 Void +0x3368 PrcbPad8 : [4 ] UChar +0x336c VendorString : [13 ] UChar +0x3379 InitialApicId : UChar +0x337a LogicalProcessorsPerPhysicalProcessor : UChar +0x337b PrcbPad9 : [5 ] UChar +0x3380 FeatureBits : Uint4B +0x3388 UpdateSignature : _LARGE_INTEGER +0x3390 IsrTime : Uint8B +0x3398 RuntimeAccumulation : Uint8B +0x33a0 PowerState : _PROCESSOR_POWER_STATE +0x3468 DpcWatchdogDpc : _KDPC +0x3488 DpcWatchdogTimer : _KTIMER +0x34b0 WheaInfo : Ptr32 Void +0x34b4 EtwSupport : Ptr32 Void +0x34b8 InterruptObjectPool : _SLIST_HEADER +0x34c0 HypercallPageList : _SLIST_HEADER +0x34c8 HypercallPageVirtual : Ptr32 Void +0x34cc VirtualApicAssist : Ptr32 Void +0x34d0 StatisticsPage : Ptr32 Uint8B +0x34d4 RateControl : Ptr32 Void +0x34d8 Cache : [5 ] _CACHE_DESCRIPTOR +0x3514 CacheCount : Uint4B +0x3518 CacheProcessorMask : [5 ] Uint4B +0x352c PackageProcessorSet : _KAFFINITY_EX +0x3538 PrcbPad91 : [1 ] Uint4B +0x353c CoreProcessorSet : Uint4B +0x3540 TimerExpirationDpc : _KDPC +0x3560 SpinLockAcquireCount : Uint4B +0x3564 SpinLockContentionCount : Uint4B +0x3568 SpinLockSpinCount : Uint4B +0x356c IpiSendRequestBroadcastCount : Uint4B +0x3570 IpiSendRequestRoutineCount : Uint4B +0x3574 IpiSendSoftwareInterruptCount : Uint4B +0x3578 ExInitializeResourceCount : Uint4B +0x357c ExReInitializeResourceCount : Uint4B +0x3580 ExDeleteResourceCount : Uint4B +0x3584 ExecutiveResourceAcquiresCount : Uint4B +0x3588 ExecutiveResourceContentionsCount : Uint4B +0x358c ExecutiveResourceReleaseExclusiveCount : Uint4B +0x3590 ExecutiveResourceReleaseSharedCount : Uint4B +0x3594 ExecutiveResourceConvertsCount : Uint4B +0x3598 ExAcqResExclusiveAttempts : Uint4B +0x359c ExAcqResExclusiveAcquiresExclusive : Uint4B +0x35a0 ExAcqResExclusiveAcquiresExclusiveRecursive : Uint4B +0x35a4 ExAcqResExclusiveWaits : Uint4B +0x35a8 ExAcqResExclusiveNotAcquires : Uint4B +0x35ac ExAcqResSharedAttempts : Uint4B +0x35b0 ExAcqResSharedAcquiresExclusive : Uint4B +0x35b4 ExAcqResSharedAcquiresShared : Uint4B +0x35b8 ExAcqResSharedAcquiresSharedRecursive : Uint4B +0x35bc ExAcqResSharedWaits : Uint4B +0x35c0 ExAcqResSharedNotAcquires : Uint4B +0x35c4 ExAcqResSharedStarveExclusiveAttempts : Uint4B +0x35c8 ExAcqResSharedStarveExclusiveAcquiresExclusive : Uint4B +0x35cc ExAcqResSharedStarveExclusiveAcquiresShared : Uint4B +0x35d0 ExAcqResSharedStarveExclusiveAcquiresSharedRecursive : Uint4B +0x35d4 ExAcqResSharedStarveExclusiveWaits : Uint4B +0x35d8 ExAcqResSharedStarveExclusiveNotAcquires : Uint4B +0x35dc ExAcqResSharedWaitForExclusiveAttempts : Uint4B +0x35e0 ExAcqResSharedWaitForExclusiveAcquiresExclusive : Uint4B +0x35e4 ExAcqResSharedWaitForExclusiveAcquiresShared : Uint4B +0x35e8 ExAcqResSharedWaitForExclusiveAcquiresSharedRecursive : Uint4B +0x35ec ExAcqResSharedWaitForExclusiveWaits : Uint4B +0x35f0 ExAcqResSharedWaitForExclusiveNotAcquires : Uint4B +0x35f4 ExSetResOwnerPointerExclusive : Uint4B +0x35f8 ExSetResOwnerPointerSharedNew : Uint4B +0x35fc ExSetResOwnerPointerSharedOld : Uint4B +0x3600 ExTryToAcqExclusiveAttempts : Uint4B +0x3604 ExTryToAcqExclusiveAcquires : Uint4B +0x3608 ExBoostExclusiveOwner : Uint4B +0x360c ExBoostSharedOwners : Uint4B +0x3610 ExEtwSynchTrackingNotificationsCount : Uint4B +0x3614 ExEtwSynchTrackingNotificationsAccountedCount : Uint4B +0x3618 Context : Ptr32 _CONTEXT +0x361c ContextFlags : Uint4B +0x3620 ExtendedState : Ptr32 _XSAVE_AREA
查看CPU数量
1 kd> dd KeNumberProcessors
查看KPCR
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 kd> dd KiProcessorBlock L2 83f b88c0 83f 79d20 00000000 kd> dt _kpcr 83f 79d20-120 nt!_KPCR +0x000 NtTib : _NT_TIB +0x000 Used_ExceptionList : 0x83f760ac _EXCEPTION_REGISTRATION_RECORD +0x004 Used_StackBase : (null) +0x008 Spare2 : (null) +0x00c TssCopy : 0x801e4000 Void +0x010 ContextSwitches : 0xbac4f +0x014 SetMemberCopy : 1 +0x018 Used_Self : (null) +0x01c SelfPcr : 0x83f79c00 _KPCR +0x020 Prcb : 0x83f79d20 _KPRCB +0x024 Irql : 0x1f '' +0x028 IRR : 0 +0x02c IrrActive : 0 +0x030 IDR : 0xffffffff +0x034 KdVersionBlock : 0x83f78c00 Void +0x038 IDT : 0x80b99400 _KIDTENTRY +0x03c GDT : 0x80b99000 _KGDTENTRY +0x040 TSS : 0x801e4000 _KTSS +0x044 MajorVersion : 1 +0x046 MinorVersion : 1 +0x048 SetMember : 1 +0x04c StallScaleFactor : 0xa20 +0x050 SpareUnused : 0 ' ' +0x051 Number : 0 '' +0x052 Spare0 : 0 ' ' +0x053 SecondLevelCacheAssociativity : 0 '' +0x054 VdmAlert : 0 +0x058 KernelReserved : [14] 0 +0x090 SecondLevelCacheSize : 0 +0x094 HalReserved : [16] 0x1000000 +0x0d4 InterruptMode : 0 +0x0d8 Spare1 : 0 ' ' +0x0dc KernelReserved2 : [17 ] 0 +0x120 PrcbData : _KPRCB
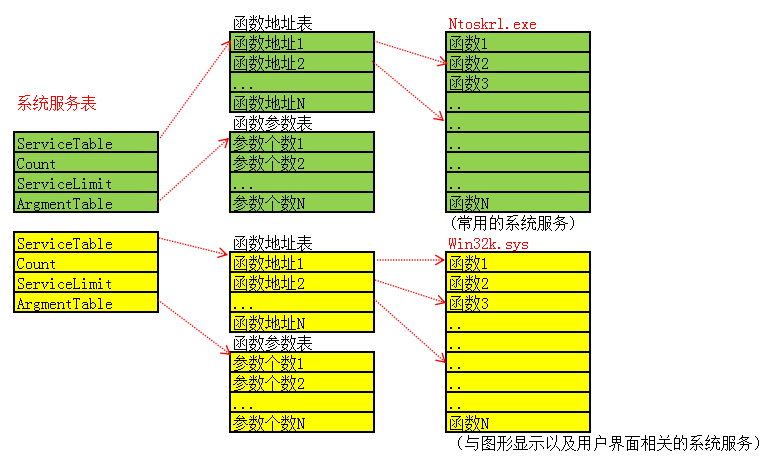
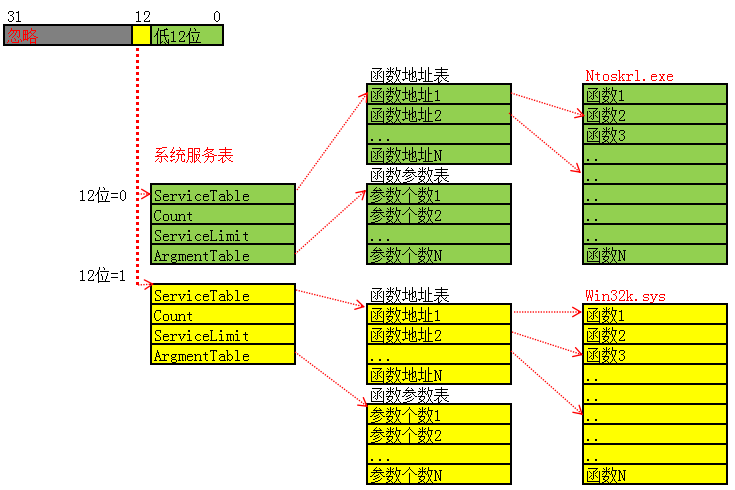
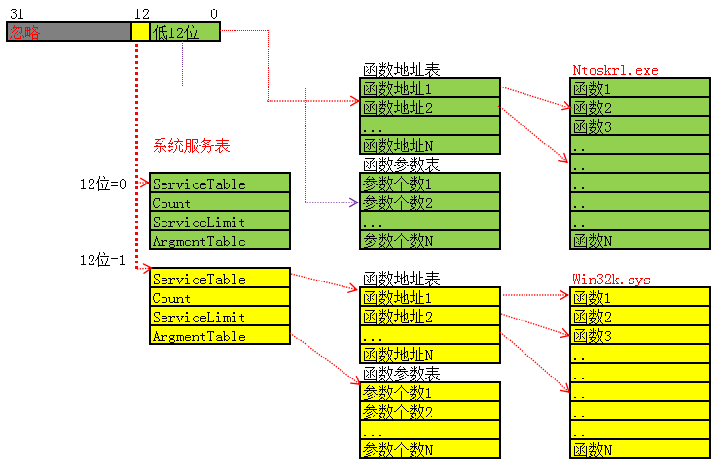
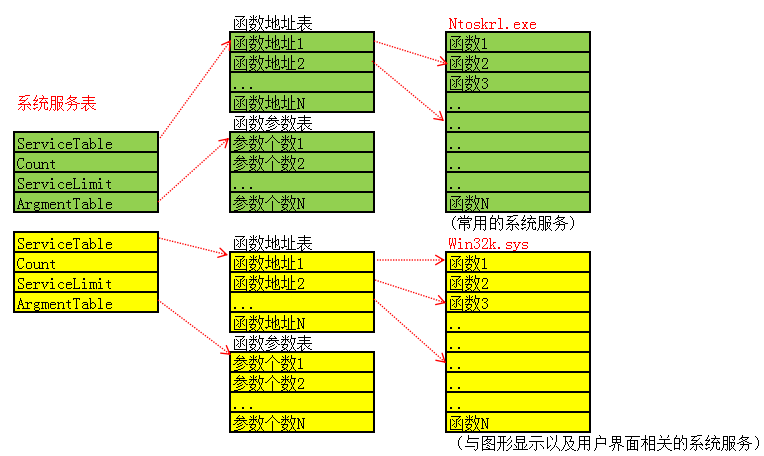
系统服务表 1、SystemServiceTable 系统服务表
2、SystemServiceTable 系统服务表位置 通过_KTHREAD+0xE0
3、判断要调用的函数在哪个表 通过服务号
4、找到要执行的函数与参数个数
SSDT 1、SystemServiceTable 系统服务表 1 2 3 4 5 6 typedef struct _KSERVICE_TABLE_DESCRIPTOR { PULONG_PTR Base; 0x0 函数表 PULONG Count; 0x4 统计这张表调用次数 ULONG Limit; 0x8 函数总个数表 PUCHAR Number; 0xc 函数参数个数表 } KSERVICE_TABLE_DESCRIPTOR
2、如何访问系统服务表呢? SSDT 的全称是 System Services Descriptor Table,系统服务描述符表
1 2 3 kd> dd KeServiceDescriptorTable(SSDT)导出的 声明一下就可以使用了 kd> dd KeServiceDescriptorTableShadow(SSDT Shadow)未导出 需要用其他的方式来查找
[!NOTE]
KeServiceDescriptorTableShadow = KeServiceDescriptorTable + 0x40
案例 SSDTHOOK Tool.h
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 #pragma once #include <ntifs.h> #include <ntstrsafe.h> #include <ntimage.h> NTSTATUS MmCreateSection ( OUT PVOID* SectionObject, IN ACCESS_MASK DesiredAccess, IN POBJECT_ATTRIBUTES ObjectAttributes OPTIONAL, IN PLARGE_INTEGER InputMaximumSize, IN ULONG SectionPageProtection, IN ULONG AllocationAttributes, IN HANDLE FileHandle OPTIONAL, IN PFILE_OBJECT FileObject OPTIONAL ) PWCH getSystemNtDllPath () ;PUCHAR MapOfViewFile (PWCH path) ;VOID unMapOfViewFile (PVOID mapBase) ;ULONG64 exportFuntionByName (char * imageBuffer, char * funName) ;
Tool.c
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 #include "Tools.h" PWCH getSystemNtDllPath () { PWCH sysPath = ExAllocatePool (PagedPool, PAGE_SIZE); memset (sysPath, 0 , PAGE_SIZE); RtlStringCbPrintfW (sysPath, PAGE_SIZE, L"\\??\\%s\\system32\\ntdll.dll" , SharedUserData->NtSystemRoot); return sysPath; } PUCHAR MapOfViewFile (PWCH path) { HANDLE fileHandle = NULL ; UNICODE_STRING fileName = { 0 }; RtlInitUnicodeString (&fileName, path); OBJECT_ATTRIBUTES ObjectAttributes; InitializeObjectAttributes (&ObjectAttributes, &fileName, OBJ_CASE_INSENSITIVE, NULL , NULL ); IO_STATUS_BLOCK IoStatusBlock; NTSTATUS status = ZwCreateFile (&fileHandle, GENERIC_READ, &ObjectAttributes, &IoStatusBlock, NULL , FILE_ATTRIBUTE_NORMAL, FILE_SHARE_READ, FILE_OPEN, FILE_NON_DIRECTORY_FILE | FILE_SYNCHRONOUS_IO_NONALERT, NULL , NULL ); if (!NT_SUCCESS (status)) { ExFreePool (path); return 0 ; } PVOID hSection = NULL ; OBJECT_ATTRIBUTES sectionAttr; InitializeObjectAttributes (§ionAttr, NULL , OBJ_CASE_INSENSITIVE, NULL , NULL ); LARGE_INTEGER InputMaximumSize = { 0 }; status = MmCreateSection (&hSection, NULL , §ionAttr, &InputMaximumSize, PAGE_EXECUTE_READWRITE, 0x1000000 , fileHandle, NULL ); if (!NT_SUCCESS (status)) { ExFreePool (path); ZwClose (fileHandle); return 0 ; } PVOID mapBase = NULL ; SIZE_T viewSize = { 0 }; status = MmMapViewInSystemSpace (hSection, &mapBase, &viewSize); ObDereferenceObject (hSection); ZwClose (fileHandle); if (NT_SUCCESS (status)) { return mapBase; } } VOID unMapOfViewFile (PVOID mapBase) { if (!mapBase) return ; MmUnmapViewInSystemSpace (mapBase); } ULONG64 exportFuntionByName (char * imageBuffer, char * funName) { PIMAGE_DOS_HEADER pDos = (PIMAGE_DOS_HEADER)imageBuffer; PIMAGE_NT_HEADERS pNt = (PIMAGE_NT_HEADERS)((ULONG)pDos + (ULONG)pDos->e_lfanew); PIMAGE_DATA_DIRECTORY pDataDir = (PIMAGE_DATA_DIRECTORY)(&pNt->OptionalHeader.DataDirectory[0 ]); PIMAGE_EXPORT_DIRECTORY pExport = (PIMAGE_EXPORT_DIRECTORY)((ULONG)pDos + (ULONG)pDataDir->VirtualAddress); ULONG64 funcAddr = 0 ; for (SIZE_T i = 0 ;i < pExport->NumberOfNames;i++) { PULONG funAddrTable = (PULONG)((ULONG)pDos + (ULONG)pExport->AddressOfFunctions); PULONG funNameTable = (PULONG)((ULONG)pDos + (ULONG)pExport->AddressOfNames); PSHORT ord = (PULONG)((ULONG)pDos + (ULONG)pExport->AddressOfNameOrdinals); SIZE_T index = -1 ; PUCHAR name = (PUCHAR)((ULONG)pDos + (ULONG)(funNameTable[i])); if (strcmp (funName, name) == 0 ) { DbgBreakPoint (); DbgPrintEx (77 , 0 , "[db]:name--%s\r\n" , name); index = ord[i]; } if (index != -1 ) { funcAddr = (ULONG)pDos + (ULONG)funAddrTable[index]; break ; } } if (!funcAddr) { KdPrint (("没有找到函数%s\r\n" , funName)); } else { KdPrint (("找到函数%s addr %p\r\n" , funName, funcAddr)); } return funcAddr; }
ssdt.h
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 #pragma once #include <ntifs.h> #include "Tools.h" #include <intrin.h> typedef struct _KSERVICE_TABLE_DESCRIPTOR { PULONG_PTR Base; PULONG Count; ULONG Limit; PUCHAR Number; } KSERVICE_TABLE_DESCRIPTOR; typedef struct _SSDTable { KSERVICE_TABLE_DESCRIPTOR ssdt; KSERVICE_TABLE_DESCRIPTOR sssdt; }SSDTable, * PSSDTable; BOOLEAN SsdtInit () ; VOID SsdtDestory () ; PSSDTable getSSDT () ; ULONG getSSDTFuntionServiceIndex (char * funName) ; ULONG_PTR SetSSDTHook (char * funName, ULONG_PTR newFunction) ;ULONG wpOff () ;VOID wpOn (ULONG cr0) ;
ssdt.c
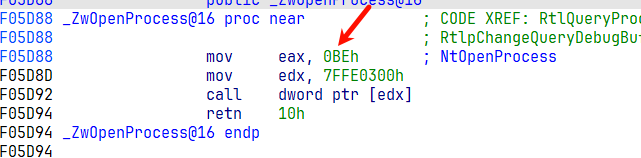
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 #include "ssdt.h" PUCHAR gMapNtdll = NULL ; extern PSSDTable KeServiceDescriptorTable; BOOLEAN SsdtInit () { if (gMapNtdll) return TRUE; PWCH path = getSystemNtDllPath (); DbgPrintEx (77 , 0 , "[db]:%S\r\n" , path); gMapNtdll = MapOfViewFile (path); ExFreePool (path); return TRUE; } VOID SsdtDestory () { if (!gMapNtdll) return ; unMapOfViewFile (gMapNtdll); gMapNtdll = NULL ; } PSSDTable getSSDT () { return (PSSDTable)((PUCHAR)KeServiceDescriptorTable + 0x40 ); } ULONG getSSDTFuntionServiceIndex (char * funName) { ULONG64 funcAddr = exportFuntionByName ((char *)gMapNtdll, funName); if (!funcAddr) return -1 ; DbgPrintEx (77 , 0 , "[db]:serviceNum---%x\r\n" , *((PSHORT)(funcAddr + 1 ))); DbgBreakPoint (); return *((PSHORT)(funcAddr + 1 )); } ULONG_PTR SetSSDTHook (char * funName, ULONG_PTR newFunction) { PSSDTable ssdTable = getSSDT (); ULONG index = getSSDTFuntionServiceIndex (funName); if (index == -1 ) return -1 ; DbgBreakPoint (); PULONG_PTR funAddr = ssdTable->ssdt.Base[index]; ULONG cr0Value = wpOff (); ssdTable->ssdt.Base[index] = newFunction; wpOn (cr0Value); return funAddr; } ULONG wpOff () { ULONG cr0 = __readcr0(); _disable(); __writecr0(cr0 & (~0x10000 )); return cr0; } VOID wpOn (ULONG cr0) { __writecr0(cr0); _enable(); }
driver.c
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 #include <ntifs.h> #include "ssdt.h" ULONG_PTR g_oldFun = NULL ; typedef NTSTATUS (NTAPI *OpenProcessProc) ( OUT PHANDLE ProcessHandle, IN ACCESS_MASK DesiredAccess, IN POBJECT_ATTRIBUTES ObjectAttributes, IN PCLIENT_ID ClientId OPTIONAL ) NTSTATUS NTAPI myOpenProcess ( OUT PHANDLE ProcessHandle, IN ACCESS_MASK DesiredAccess, IN POBJECT_ATTRIBUTES ObjectAttributes, IN PCLIENT_ID ClientId OPTIONAL ) DbgPrintEx (77 , 0 , "[db]:ZwOpenProcess HOOK.....\r\n" ); OpenProcessProc fun = (OpenProcessProc)g_oldFun; return fun (ProcessHandle,DesiredAccess,ObjectAttributes,ClientId); } VOID DriverUnload (PDRIVER_OBJECT pDriver) SetSSDTHook ("ZwOpenProcess" , g_oldFun); SsdtDestory (); LARGE_INTEGER time = { 0 }; time.QuadPart = -10000 * 3000 ; KeDelayExecutionThread (KernelMode, FALSE, &time); } NTSTATUS DriverEntry (PDRIVER_OBJECT pDriver, PUNICODE_STRING pReg) SsdtInit (); g_oldFun = SetSSDTHook ("ZwOpenProcess" , myOpenProcess); pDriver->DriverUnload = DriverUnload; return STATUS_SUCCESS; }